Security
React2Shell: What Businesses Need to Know About This Critical Security Threat in 2025
Dec 11, 2025
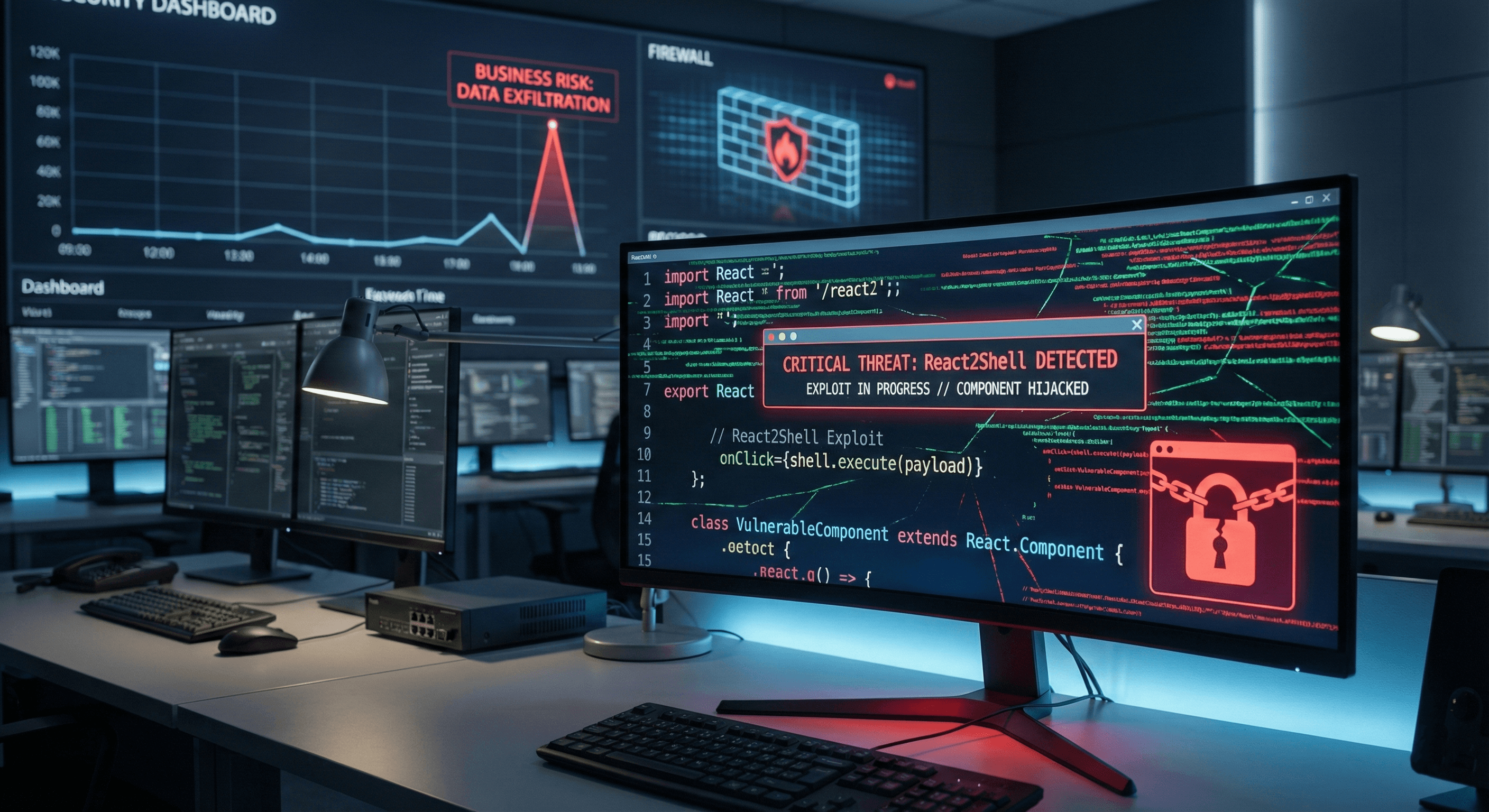
Have you audited your React or Next.js applications for vulnerabilities recently, and do you feel confident your server components are secure?
React has become one of the most widely used technologies for building modern web applications. From startups to large enterprises, thousands of businesses rely on React and its ecosystem to deliver fast, interactive digital experiences. But in late 2025, a new and serious vulnerability shook the developer community. The issue, known as React2Shell, revealed how easily attackers could compromise unpatched systems running React Server Components.
This vulnerability is more than a simple bug. React2Shell opens the door for attackers to execute arbitrary code directly on a server, potentially gaining full control of critical infrastructure. The scale and severity of this issue mean that businesses need to understand what it is, how it works, and what steps to take immediately.
What Is React2Shell?
React2Shell refers to a remote code execution flaw affecting React Server Components (RSC), specifically within certain versions of React 19 and frameworks built on top of it, such as Next.js. The vulnerability stems from how React processes certain server-side requests. In specific conditions, the server fails to properly validate and sanitize incoming data, allowing attackers to craft special requests that trigger code execution.
What makes this vulnerability particularly dangerous is that it does not require authentication. A malicious actor can simply send a specially crafted HTTP request to an affected endpoint and exploit the system.
Why Businesses Should Pay Attention
Even if your organization does not use React Server Components directly, you may still be affected. Many frameworks and tools rely on RSC under the hood, including:
Next.js applications
React Router applications using server-side rendering
Third-party libraries that integrate RSC features
Custom React-based backend rendering solutions
Because React2Shell impacts the server layer, a successful attack could lead to severe consequences, such as:
Full server compromise
Data theft or corruption
Deployment of malware or ransomware
Interruption of critical business operations
This vulnerability has been assigned a CVSS score of 10.0, the highest severity rating. This means that unpatched systems are at immediate risk, and exploitation attempts are already being observed in the wild.
How Attackers Are Exploiting It
Shortly after the vulnerability became public, threat groups began scanning the internet for exposed systems. These scans look for common URLs and API endpoints associated with React Server Components. Once a vulnerable endpoint is found, an attacker can send a malicious payload that triggers the remote code execution flaw.
In real-world incidents, attackers have used React2Shell to:
Install crypto-miners
Deploy unauthorized remote shells
Extract environment variables containing credentials
Access internal systems through pivoting
Because many deployments lack strict boundary controls, a single vulnerable endpoint can compromise an entire application environment.
What Organizations Should Do Right Now
If your applications use React Server Components or frameworks that depend on them, you should take action immediately. Here’s what we recommend:
1. Audit Versions and Dependencies
Check your package versions for React, Next.js, and related libraries. Identify where React Server Components are used, either directly or indirectly.
2. Apply Security Patches
Updated and patched versions are available. Upgrading React and your framework to the latest stable release should be your first step.
3. Review Deployment Environments
Make sure your production environment is running the patched versions. Update your CI/CD pipelines to prevent deploying outdated packages.
4. Strengthen Monitoring and Logging
Enable detailed logs and alerts for unusual server-side behavior, especially for endpoints that receive untrusted input.
5. Conduct a Security Assessment
Review your entire application architecture for similar vulnerabilities and misconfigurations. React2Shell may expose deeper issues in access control, dependency management, or deployment pipelines.
Conclusion
React2Shell is a reminder that even popular, well-maintained technologies can introduce serious risks. As attackers continue to adopt automated tools and AI-driven scanning, vulnerabilities like this will be exploited faster than ever. Businesses that rely on React or Next.js should treat this as a priority and ensure their systems are fully patched and monitored.
If your team is unsure whether you’re affected, or if you need help auditing, patching, or securing your applications, Team Vienna can support you in fixing the issue and strengthening your overall security posture. Staying ahead of vulnerabilities is no longer optional, it’s essential.
Ready to Transform Your Business?
